Perle P-Ring Protocol
Preventing a switch loop scenario and enabling communication if a failure occurs in the ring
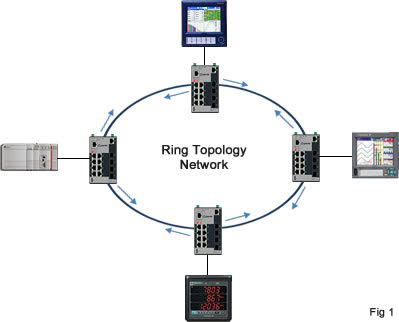
The Ring Topology: In a ring network each Ethernet switch is connected to two other switches forming a ring. This provides two benefits:
- Each switch has a redundant connection (link) into the network.
- The cabling infrastructure is more cost effective than using an aggregation switch at a central location.
For these reasons, ring topology networks are popular within industrial infrastructures (Fig 1).
Caution! Storm Warning: However, when using switches to set up a ring topology network, the administrator must ensure they do not introduce a “switch loop” condition that creates broadcast storms. The storms occur when broadcasts and multicasts are forwarded by switches out every port. If a destination for the message cannot be found, the switches will repeatedly rebroadcast the packets and flood the network. Since the Layer 2 header does not support a time to live (TTL) value, a packet can loop forever consuming all available bandwidth. This condition can block all other network traffic and will eventually result in a network meltdown.
Spanning Tree to the rescue? One resolution to this problem is to simply break the loop somewhere in the ring. Spanning Tree protocols such as RSTP were developed to detect these switch loop conditions and then intelligently reconfigure the network to provide this break, eliminating the switch loop. Also, if anything happens in the network, a topology change notification is sent out to create a different safe path.
Spanning Tree protocols, such as RSTP, can recover in a matter of seconds and are effective solutions for many networks.
One of the difficulties in using spanning tree for simple ring networks is the fact that configuration is hard. The selection of the Root Bridge, the configurable priority number, the path cost, BPDU guard, BPDU Filter, to name a few, add to the complexity. So many details for such a simple network!
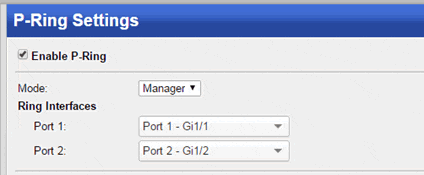
Perle’s P-Ring feature, available on all IDS Managed Switches, eliminates this hassle by providing an easy to use method for configuring a ring network that uses standard spanning tree protocols.
When configuring P-Ring, through the web manager or CLI, simply check “Enable P-Ring”, Then, select the ring ports and specify whether the switch performs as the “root” ( “Manager” ) or “ Client”. That’s it! You can now install a safe, loop free ring network.