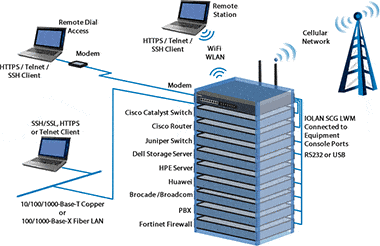
Securing your IoT network devices
By Max BurkhalterNovember 24, 2020
If you've implemented Internet of Things (IoT) networks and devices, you need to ensure that they and all data collected and transmitted are secure. Configuring how these devices to connect to and interact with your systems is vital.
Code checks
The first component to check in your network infrastructure is your code. IoT devices are typically small and sensor-based, and the code is rudimentary at best. Use testing to identify and stop memory leaks, or tamp down buffer overflow to reduce vulnerability. Stack cookies, which are random data strings, can be coded to override in case of buffer overflows. If the overwritten cookie doesn't match the source code the application will terminate. Atera notes that this can be extremely helpful if you have remote employees using IoT devices.
Access control
Devices shouldn't have the ability to initiate access to your network; only the network should be able to initiate contact with devices. The one-way permission can help prevent someone from accessing your database by hacking an IoT humidity monitoring system. Implementing context-aware access controls that regulate connectivity as well as command and data transfer levels can help with security. You can force connections to IoT devices to pass through a jump host and/or network proxy in a funnel point. By inspecting network traffic at this point, you can make the determination as to whether the payloads being carried are correct for each device.
Vendor compliance
Organizations that buy services from contractors often end up with IoT devices on their premises, such as security and HVAC systems. These should meet your own rigorous standards for security to prevent them from making you vulnerable to hacking. Ensure that you, not your vendors, control access to your network. Typical devices that might be vendor-side supplied and maintained include:
- Wireless access points
- Security systems
- IP cameras (the most commonly hacked IoT device, according to ZD Net.)
- Printers
- Medical devices
- Refrigerators
- Temperature control systems
- Energy use monitors
Identify all devices
Every IoT device should have a unique name and ID number. Don't rely on presets. Hacking is so much easier when passwords are left on default, or devices are named after their function or a room number. You'll need to be able to verify the identity of the IoT devices that you're communicating with at any given time, and identify if the actions the device is taking meet your preset parameters for access and behavior. Failure to correctly manage your IoT devices from the very beginning will make your company vulnerable to spoofing or hacking.
Split your network
If desired, you can put all IoT devices on their own secure network. This significantly limits exposure, and anyone hacking in through a singular device will still have problems reaching your mainframe. Have a single access point between networks and ensure it is firewalled. Only allow specific people within your organization the ability to control that access point. Creating a sealed environment to segregate your IoT devices will demand creating a virtual LAN and a separate service set identifier. This "guest network" can also be used for all vendor supplied devices.
Secure your supply chain
If your IoT devices run across your supply chain and there are multiple points of access from multiple parties, such as technology vendors, product or services suppliers, and sales or service customers, you should have a regular quarterly discussion with the staff in charge of the supply chain and your IT security contingent. Make sure all new IoT devices are reviewed and approved before purchase, and that setup and initialization is handled promptly.
By ensuring every device connecting to your network is secure, you can reduce cybersecurity risks and prevent some types of hacking. Contact us today to learn more about how Perle supports IoT devices and networks.